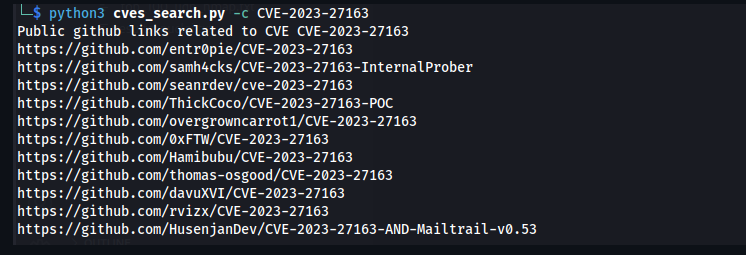
Happy to share github_cves_search project: a script to discover public GitHub exploits for specific CVEs! This tool, available at , allows you to find GitHub exploits related to a particular CVE by extracting information from...
Author - AdminStar@
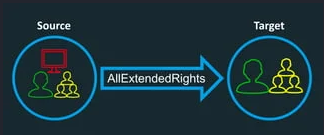
Hello all, recently I’ve faced an issue during an active directory pentest where the resolution allows me to learn something more. Hereby I am sharing how to exploit AllExtendedRights ACL between nodes in Active...
OSINT is a crucial phase in a pentest as it provides valuable insights and information about the target organization’s digital footprint, potential vulnerabilities, and attack surface. By gathering intelligence from...
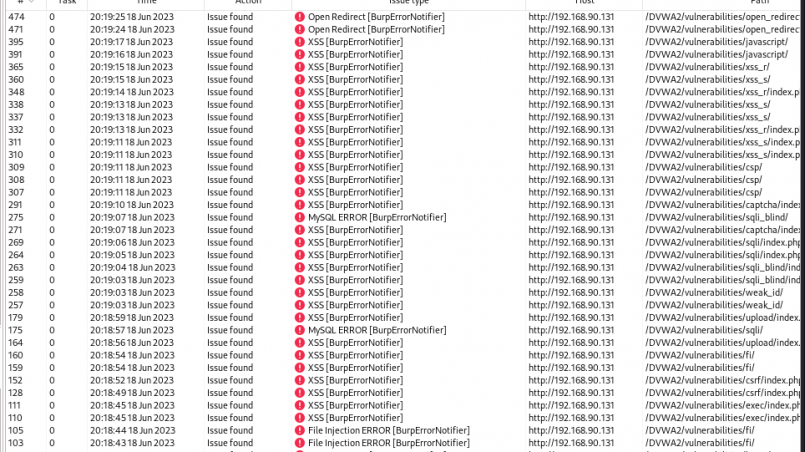
I am excited to announce the release of payload_launcher, a cutting-edge custom BurpSuite plugin developed by myself in Python that streamlines the process of identifying web vulnerabilities. With payload_launcher, you no longer...
1. Filter by IP address: “ip.addr == x.x.x.x”, where “x.x.x.x” is the IP address you want to filter 2. Filter by IP address range: “ip.addr >= x.x.x.x and ip.addr <= y.y.y.y”, where...
10 plugins useful for web penetration testing : Plugin 1 : H1 Report Finder Usage: Finds public security reports published on Hackerone Link of the repository : Plugin 2 : WordPress Scanner Usage: Finds known vulnerabilities in...
Summary of open source tools of the week I dedicated this week (from february 06th to february 10th 2023) to present opensource tools in coordination with penetration testing, below is the summary: Tool 1 : crackmapexec Usage:...
In a penetration testing engagement, after having a low shell, the next step is to get the administrator or system privilege. It can be done through kernel exploit; this is where WES-NG enters in the game… WES-NG is a tool...
IntelSpy is a multi-threaded network intelligence tool which performs automated network services enumeration. In an automated way, it performs live hosts detection scans, port scans, services enumeration scans, web content scans...
Jok3r is a Python3 CLI application which is aimed at helping penetration testers for network infrastructure and web black-box security tests. The goal is to save as much time as possible during network/web pentests by automating...