Recently, I’ve discovered a new way to escalate privilege on windows through WSUS when HTTP protocol is used instead of HTTPS.
In this quick explanation I’ll describe what WSUS is, explain how to detect the vulnerability and how to exploit it.
- What is WSUS
WSUS works as a Windows Server role; it is a software application provided by Microsoft to enable administrators to manage the distribution of updates and patches for the Microsoft software products to the computers in their network. One or more WSUS servers can be deployed depending on the number of client machines and the organization’s IT network. - How to detect that vulnerability ?
If we have the power to modify our local user proxy we therefore have the power to escalate our privilege to Administrator if the below conditions are met:
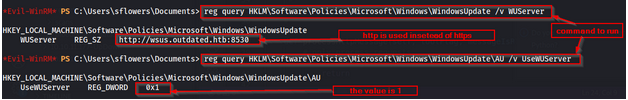
The updates are not requested using httpS but http. The following command may help to check whether http or https is used:
reg query HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate /v WUServer
The registry subkey located at HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate\AU\UseWUServer should exist and equal to 1
The following command may help to the value of the subkeys UseWuServer:
reg query HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate\AU /v UseWUServer
Below is an example of these requirements set :
- How to detect that vulnerability ?
This vulnerability can be exploited by using SharpWSUS tool available at https://github.com/nettitude/SharpWSUS


