In a penetration testing engagement, after having a low shell, the next step is to get the administrator or system privilege. It can be done through kernel exploit; this is where WES-NG enters in the game…
WES-NG is a tool based on the output of Windows’ systeminfo utility which provides the list of vulnerabilities the OS is vulnerable to, including any exploits for these vulnerabilities. Every Windows OS between Windows XP and Windows 11, including their Windows Server counterparts, is supported.
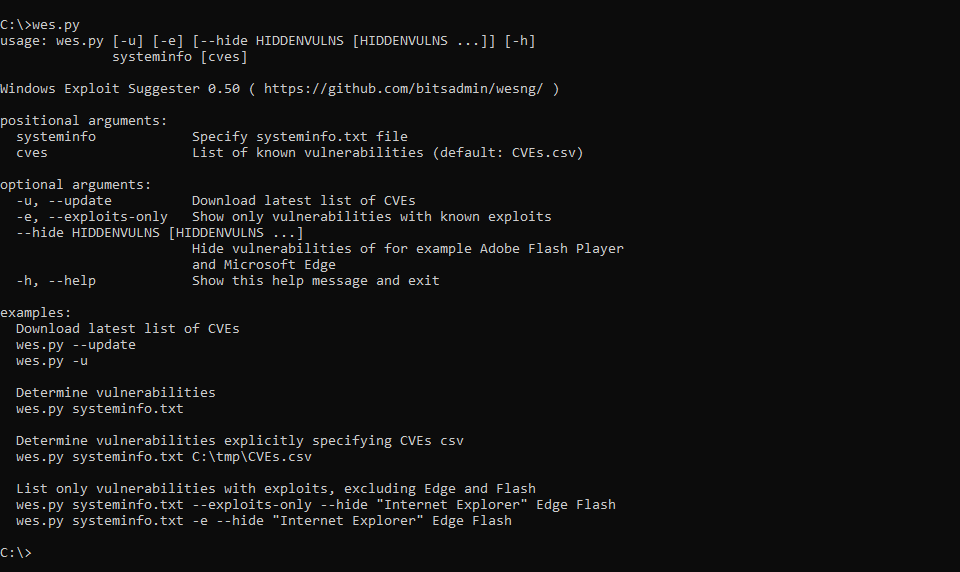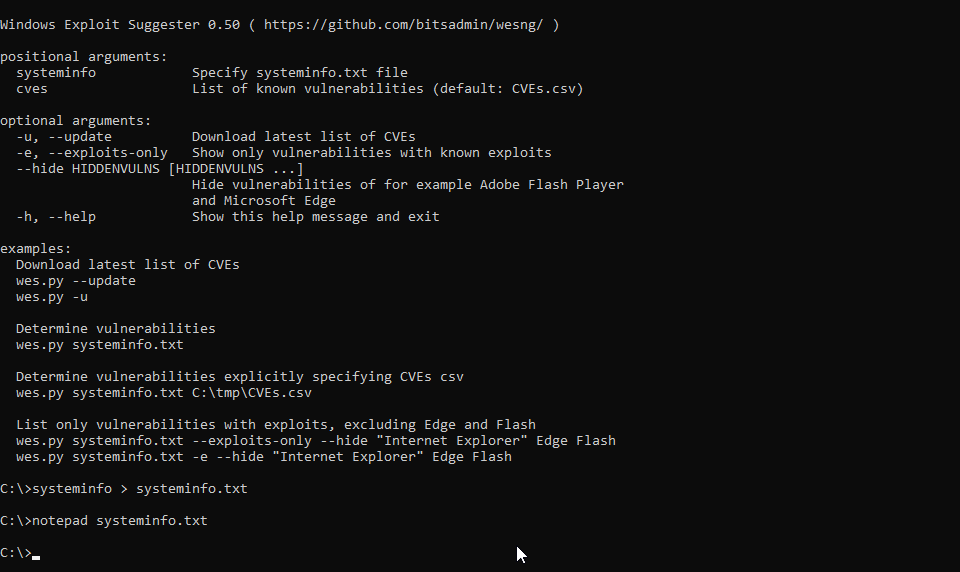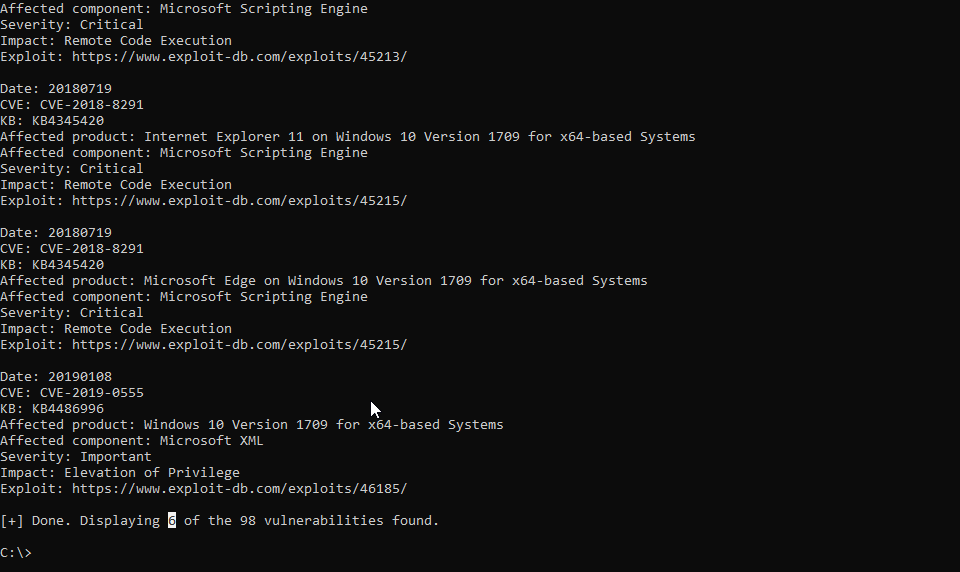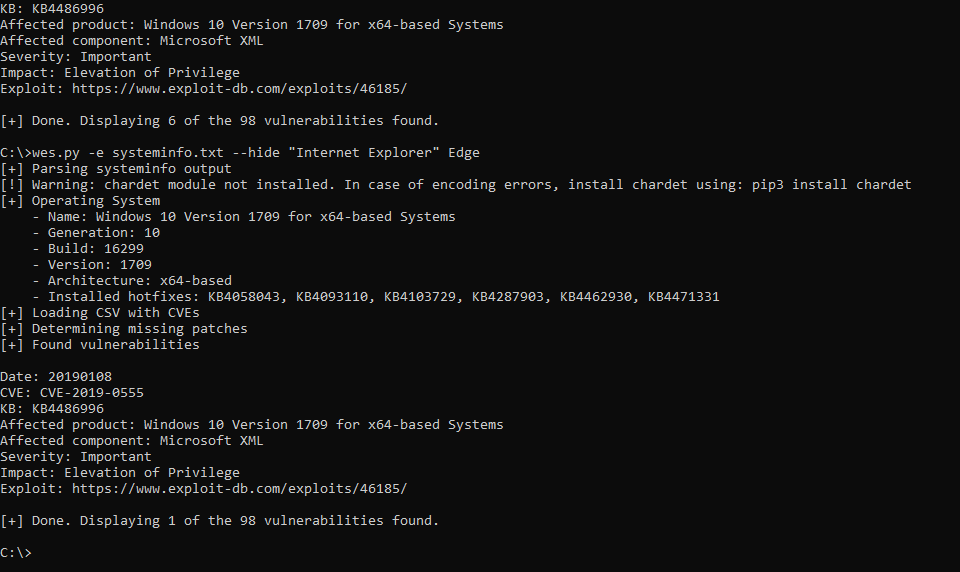
The link to get it is https://github.com/bitsadmin/wesng.
~Enjoy
#offensivesecurity #penetrationtesting #enumeration #exploitation #privilegeescalation #kernelexploit #windows #python #opensource

