SQL Injection whitebox approach (part2)
In the part 1 of this serie, we worked on :
- Identification of the files we want to deal with;
- Defining the pattern we will be looking for in the file, for us to inject our payload (GET, POST, REQUEST);
- Enabling Database logging.
In this part, we will focus on the python script that will send the request to the identified pages with the required parameters.
For demonstration purposes, we will work with version 2.2.1 of ATutor available at https://sourceforge.net/projects/atutor/files/atutor_2_2_1/.
The script does the following actions:
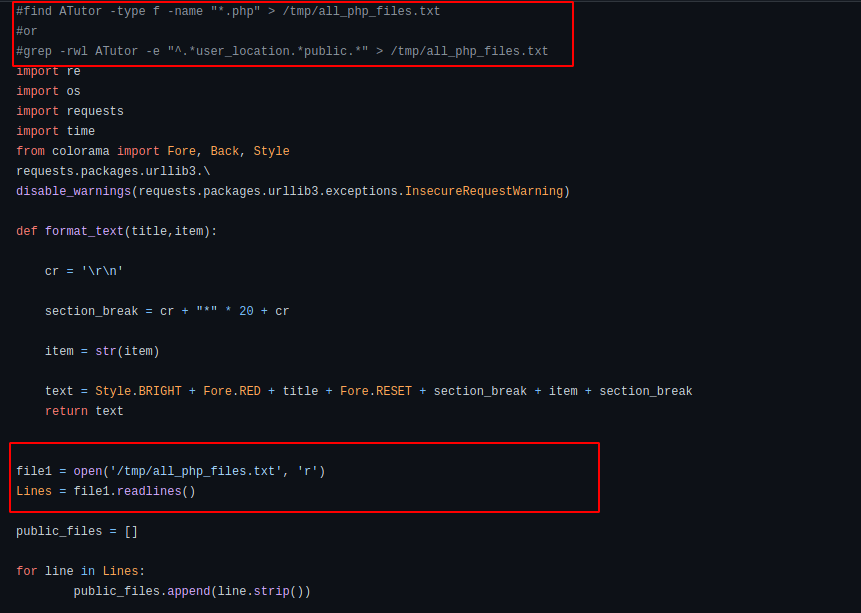
- Open the file containing the list of all the pages to which the sql injection should be tested. Finding those pages can be done via a simple find command but as many of them will require authentication, we can reduce the number of pages to be tested by looking only at public accessible pages. This task is left as an exercise to be done to the reader.
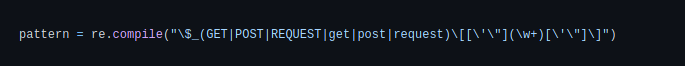
- For each file of this list, detect all GET, POST or REQUEST methods ($_GET[…], $_POST[…] and $_REQUEST[…]) with regex.
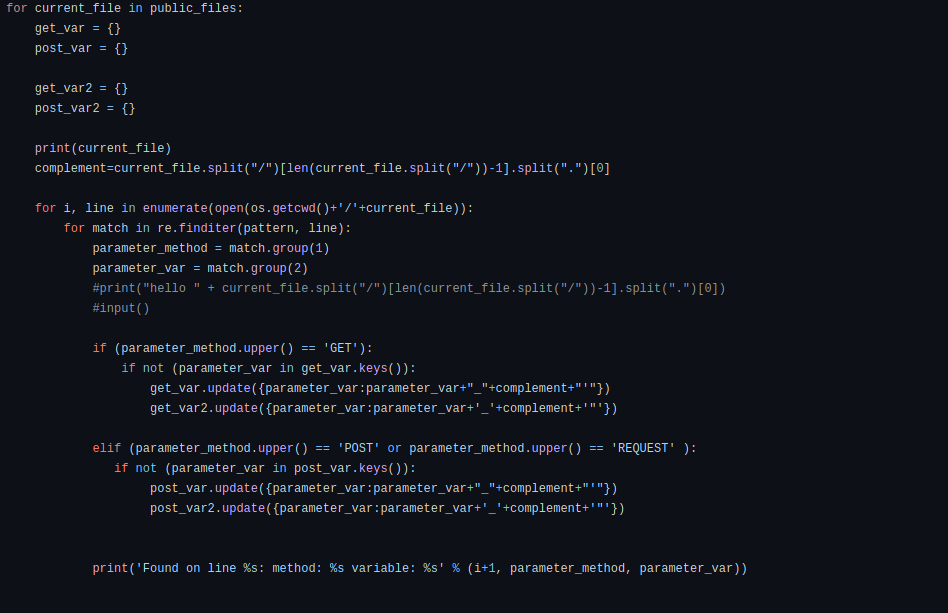
- For each method listed ahead send a parameter with single quote and another parameter with double quote followed by the name of the page. If the page name is named for example test.php and content $id = $_GET[‘id’] = ; we will send the following two GET request:
test.php?id=id_test’
test.php?id=id_test”
An SQLi can be triggered whether by a single or a double code, depending on how the code is written, that is the reason why two requests are sent, one with a simple quote, the second with a double quote.If the id parameter is within a POST or REQUEST method, then a POST request will be sent instead of a GET request.
Assuming the filename is friends.php there’s an name parameter (GET method), search parameter (POST method) and id parameter (REQUEST method), then will will have to send 2 requests (2 via GET and the 2 others via POST):
GET request
friends.php?name=name_friends’
friends.php?name=name_friends”POST request
friends.php?search=search_friends’&id=id_friends’
friends.php?search=search_friends”&id=id_friends”
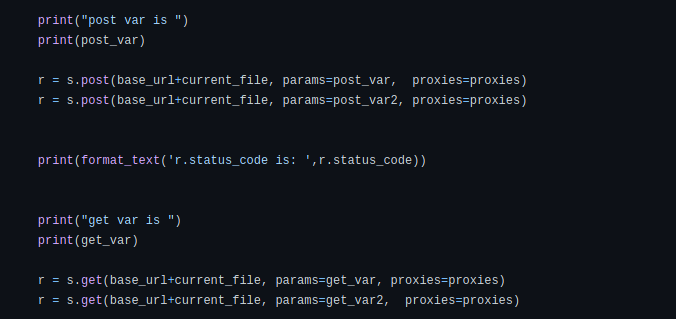
- In order to see what we are sending through BurpSuite, every request is sent via proxies parameter which is equal to {“http”:”http://127.0.0.1:8000”}
The full code is available at https://github.com/lucsemassa/sqli_detect/blob/main/test_sql_white_box_approach.py and should be included in the base folder of the web project (here in /var/www/html/ATutor).
To run the script, we just need to type cd /var/www/html/ATutor && python3 test_sql_white_box_approach.py making sure we have all the required python library.

