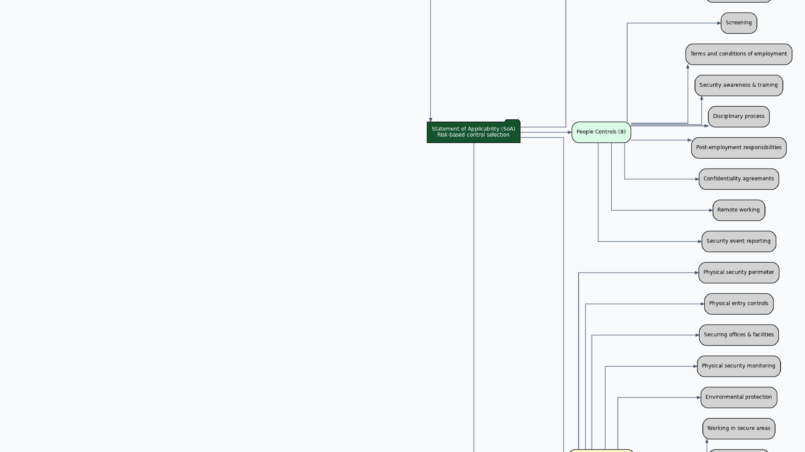
This mindmap presents a structured overview of the implementation of an Information Security Management System (ISMS / SMSI) in accordance with ISO/IEC 27001, following a Lead Implementer (LI) perspective. It illustrates the...
Author - AdminStar@
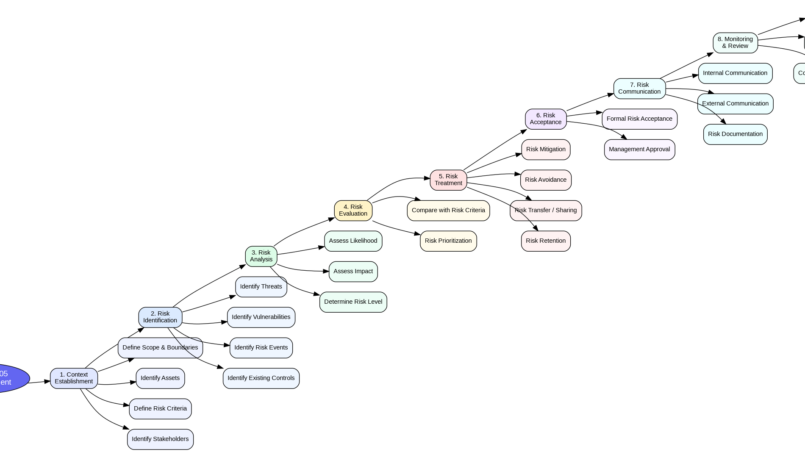
This mindmap summarizes the ISO/IEC 27005 risk assessment process by presenting its main steps and how they are logically connected. It starts with context establishment, where the scope, assets, stakeholders, and risk criteria...
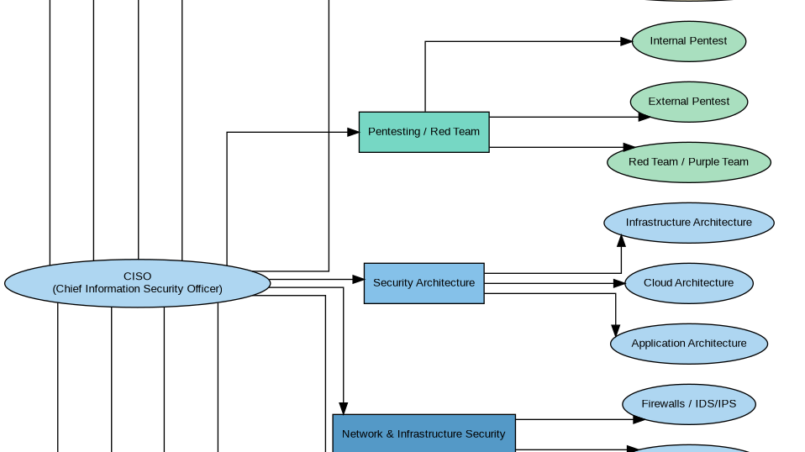
This mindmap provides a high-level overview of the main security domains a Chief Information Security Officer (CISO) typically reviews within a company.It illustrates how cybersecurity is not limited to technical controls, but...
Active Directory (AD) remains one of the most targeted components of corporate infrastructures. Due to its central role in authentication, authorization, and trust management, a single weakness in AD can quickly lead to full...
Investigations can be time-sensitive and complex. Having a set of ready-to-use queries helps me quickly filter through large volumes of data to identify suspicious activities and potential threats. This cheat sheet is meant to...
My OSIR and OSTH journey began on May 12th, when I received the annual OffSec voucher. I had been wanting to dive into OSIR for a while since it’s based on Splunk—a widely used SIEM that I hadn’t yet had the chance to...
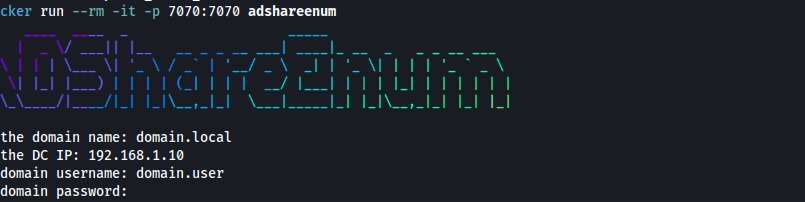
During internal assessments or red team engagements, identifying misconfigured shares in an Active Directory environment is a key step for privilege escalation and lateral movement. That’s why I built ADShareEnum, a Dockerized...
My CISSP journey began in July 2024 when I started online training with an online training company. I have always aspired to hold a managerial position in IT security, such as a CISO. In order to reach that position, I realized...
Recently, I was working on an Active Directory lab where the challenge was to extract a password stored in a user’s description field. I successfully completed the task using CrackMapExec on my primary computer. However...
I am happy to share hereby my success story with the OSDA certification. If you are aiming to pass this certification, my journey of preparation and overcoming the examination challenges may offer you valuable insights. This text...