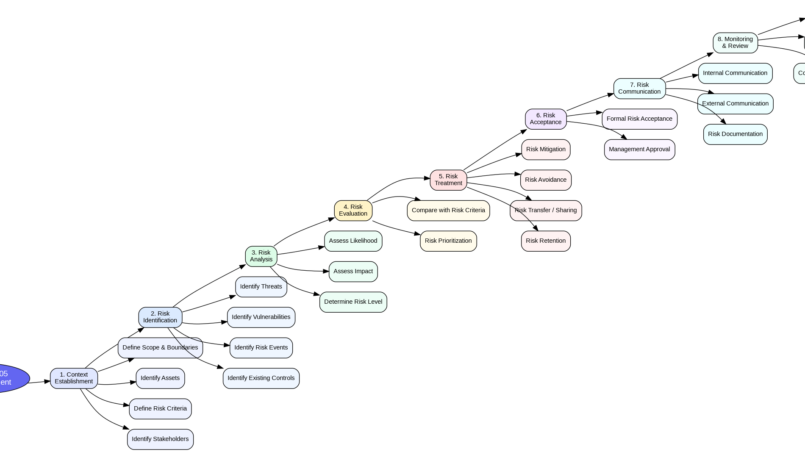
This mindmap summarizes the ISO/IEC 27005 risk assessment process by presenting its main steps and how they are logically connected.
It starts with context establishment, where the scope, assets, stakeholders, and risk criteria are defined. Based on this context, risk identification focuses on threats, vulnerabilities, risk events, and existing controls. These risks are then analyzed by assessing likelihood, impact, and overall risk level.
The risk evaluation step compares identified risks against defined criteria to support prioritization and decision-making. Risk treatment follows, outlining possible options such as mitigation, avoidance, transfer, or retention. Once treatment decisions are made, risks are formally accepted and approved by management.
Throughout the process, risk communication and documentation ensure that relevant stakeholders are informed, while monitoring and review support continuous improvement and adaptation to changes.
This visual representation helps structure ISO 27005 – aligned risk assessments and facilitates communication between technical, risk, and business stakeholders.
It includes:
-
Context Establishment
-
Risk Identification
-
Risk Analysis
-
Risk Evaluation
-
Risk Treatment
-
Risk Acceptance
-
Risk Communication & Consultation
-
Risk Monitoring & Review
Download the file that generate the mindmap (graphviz tool format)