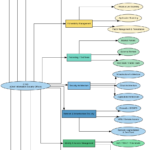
Active Directory (AD) remains one of the most targeted components of corporate infrastructures. Due to its central role in authentication, authorization, and trust management, a single weakness in AD can quickly lead to full domain compromise.
To help security professionals better understand and structure AD attacks, Orange Cyberdefense has published an Active Directory Pentest Mindmap, a comprehensive visual reference that maps the most common attack paths, techniques, and misconfigurations used during real-world penetration tests.
What this mindmap covers
This mindmap provides a structured overview of the main phases and attack categories involved in Active Directory compromise. Below is a high-level summary of the key attack areas.
- No credential attacks
- Attacks with valid user
- Quick compromise
- Man In The Middle (Listen and Relay)
- Cracking hash
- Pivoting with valid credentials
- Low access privilege escalation
- Known vulnerabilities authenticated attack
- ACLs/ACEs permissions
- Kerberos Delegation
- ADCS
- SCCM
- Admin access
- Lateral move
- Domain admin
- Trusts
- Persistence
this mindmap
-
is a single visual reference for AD pentesting
-
helps structure red team engagements
-
is useful for blue teams to understand attack paths
-
is excellent support for training and awareness
Whether you are a pentester, SOC analyst, or system administrator, this mindmap helps visualize how small misconfigurations can chain into a full domain takeover.
Download & View the Mindmap
You can download and embed the original mindmap file directly on this blog for offline viewing or presentations.
-
File format: Excalidraw SVG
-
Author: Orange Cyberdefense
👉 Official link:
https://orange-cyberdefense.github.io/ocd-mindmaps/img/mindmap_ad_dark_classic_2025.03.excalidraw.svg