Recently, I was working on an Active Directory lab where the challenge was to extract a password stored in a user’s description field. I successfully completed the task using CrackMapExec on my primary computer. However, when I had to present the same lab to a community, my computer was not responding due to a Python package issue. I had to switch to another laptop for the presentation.
Unfortunately, CrackMapExec on that computer was not up to date, and while enumerating users, I wasn’t getting the same results—specifically, I couldn’t retrieve user descriptions. Below is a screenshot showing the output.
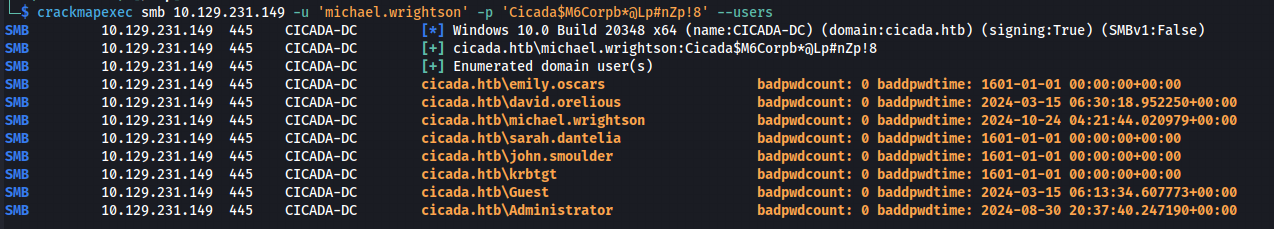
I tried other tools like GetADUsers.py and Windapsearch.py, but still couldn’t get the results I needed. These are common tools I use alongside PowerView (my favorite), which requires running in a PowerShell session.
Finally, a friend helped me by using the enumdomusers command from rpcclient. However, I knew there was a simpler and more customizable way to enumerate using ldapsearch. After the presentation, I made it my task to explore this further, and I’m happy to share a trick that may save you time. In this article, I will explain what ldapsearch is and show some use cases that can be useful during enumeration.
1. What is ldapsearch?
ldapsearch is a command-line utility used to perform LDAP (Lightweight Directory Access Protocol) searches. It is part of the OpenLDAP or LDAP utilities packages and is used to query and retrieve information from an LDAP directory server, such as Active Directory, OpenLDAP, or other directory services that support LDAP.
On Linux, you can install it by running:
sudo apt install ldap-utils
2. How it helped me solve my lab
To recap, the challenge was to extract passwords stored in the description field of users, which is not commonly retrieved by default by tools like GetADUsers.py or Windapsearch.py.
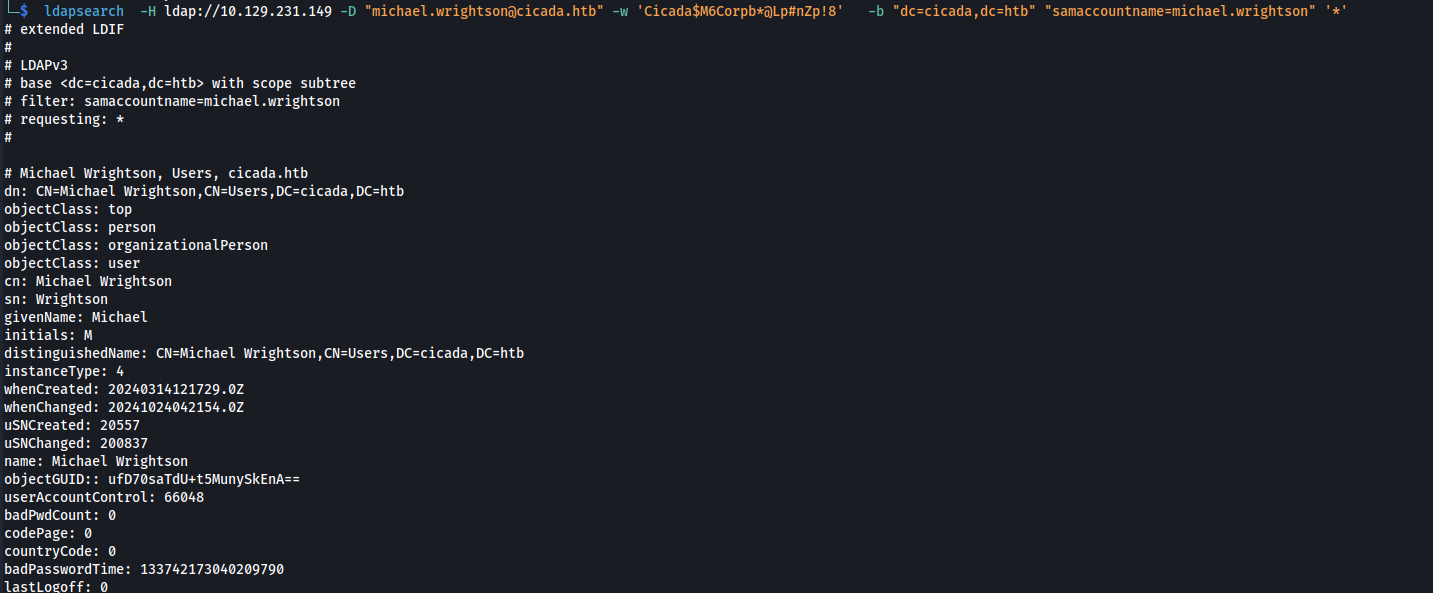
First, I tried to retrieve information about a specific user:
ldapsearch -H ldap://10.129.231.149 -D “michael.wrightson@cicada.htb” -w ‘Cicada$M6Corpb*@Lp#nZp!8’ -b “dc=cicada,dc=htb” “samaccountname=michael.wrightson” ‘*’
Then, to list all AD users and their descriptions, I used the following lines :ldapsearch -H ldap://10.129.231.149 -D “michael.wrightson@cicada.htb” -w ‘Cicada$M6Corpb*@Lp#nZp!8’ -b “dc=cicada,dc=htb” “(objectClass=user)” ‘*’
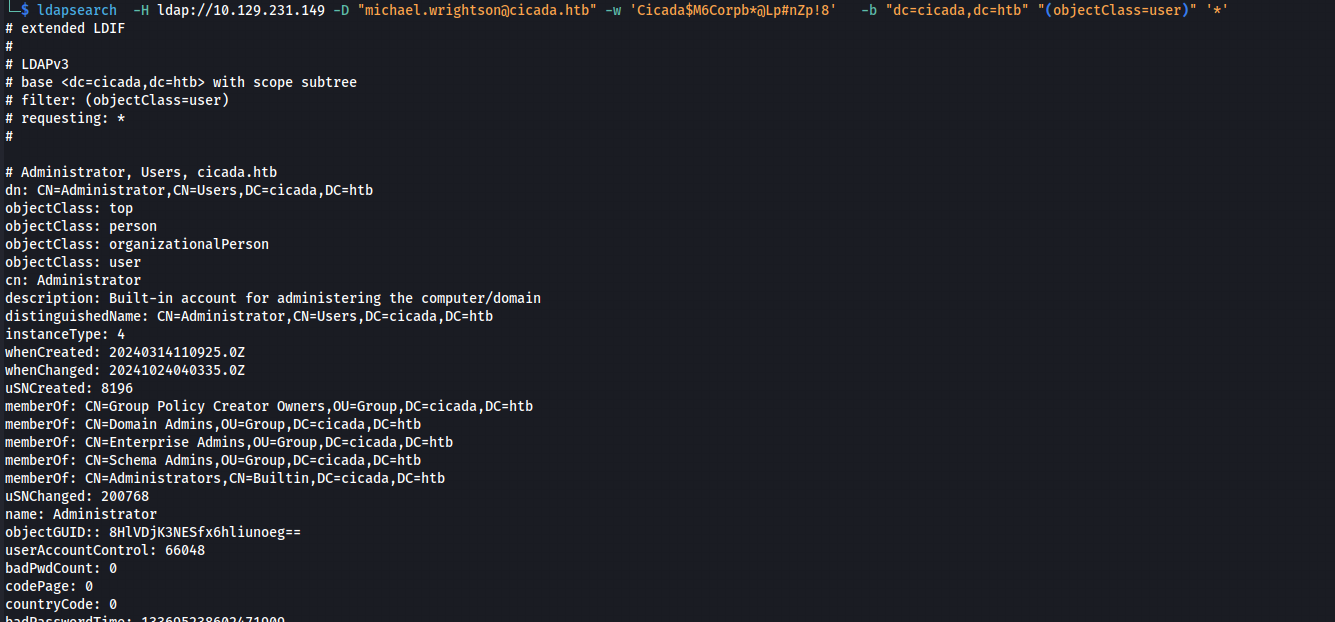
Explanation of the Options:
-H: The URI (LDAP Uniform Resource Identifier) of the LDAP server.
-D: The distinguished name (in this case, my email).
-w: The password for authentication.
-b: The base DN (in this case, dc=cicada,dc=htb).
‘*’: To display all attributes of the users.
You can filter specific fields (like description) instead of using ‘*’, which shows all attributes. To get only users with the description field, I refined the filter:
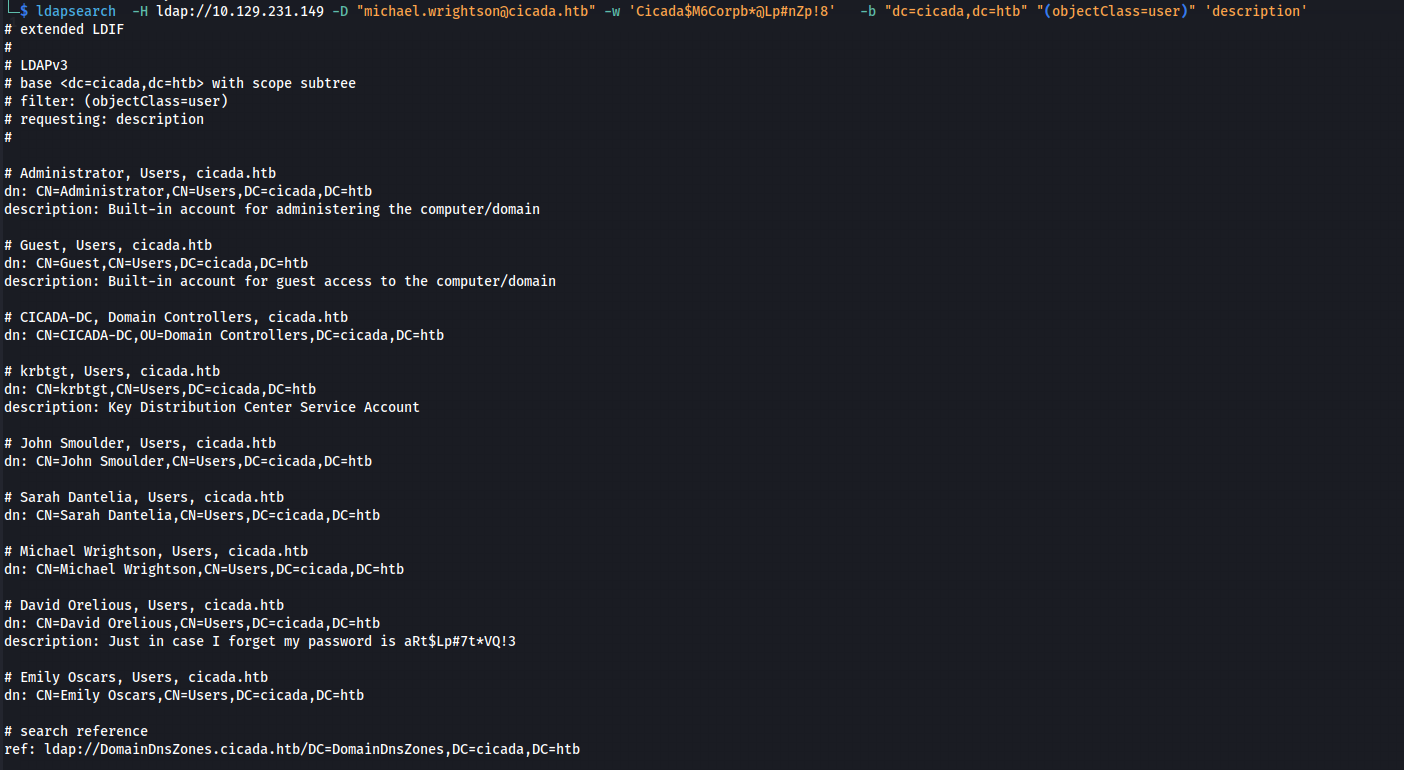
The following filter “(&(objectClass=user)(description=*))” showed users who had descriptions, making it easier to find what I was looking for. More information about filter can be found here.
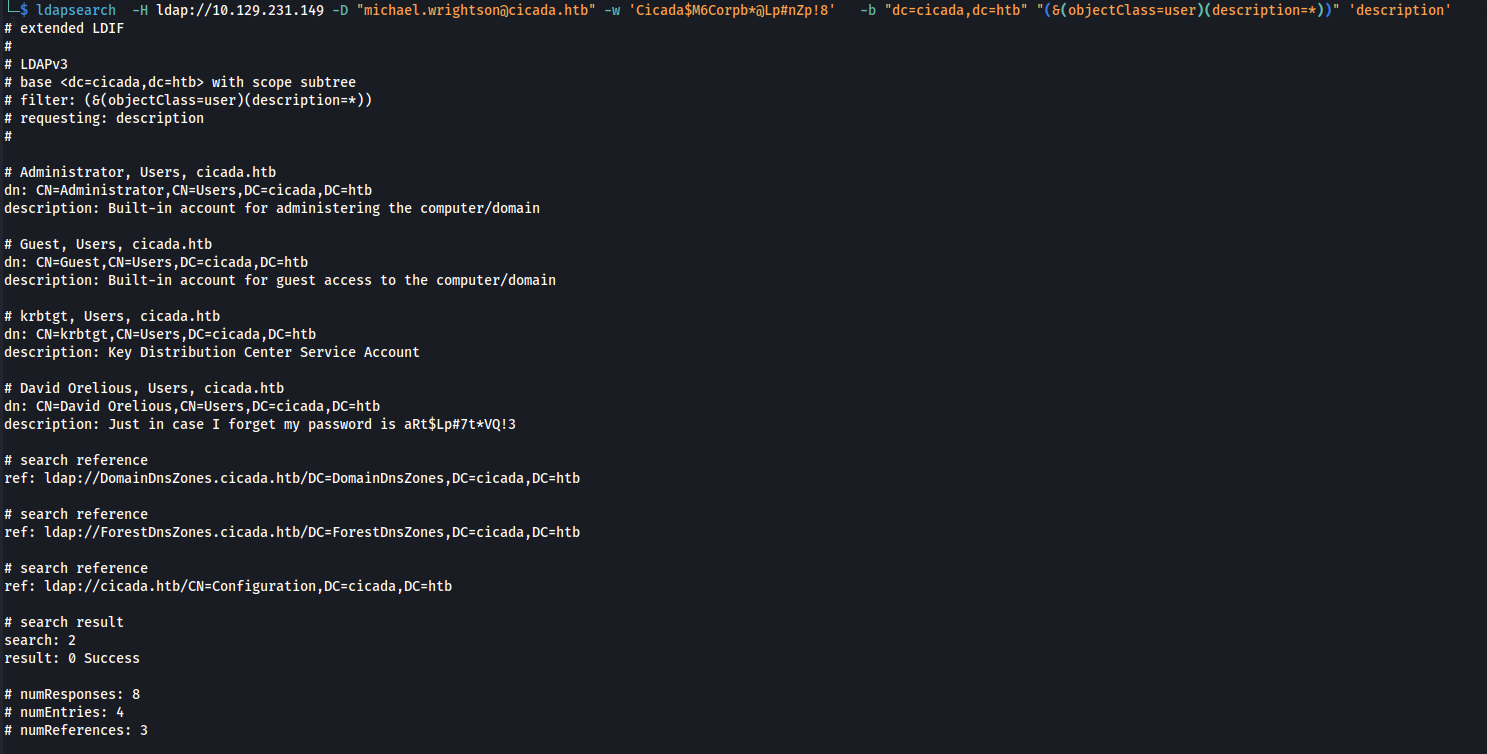
To further exclude built-in accounts, I used the following filter:
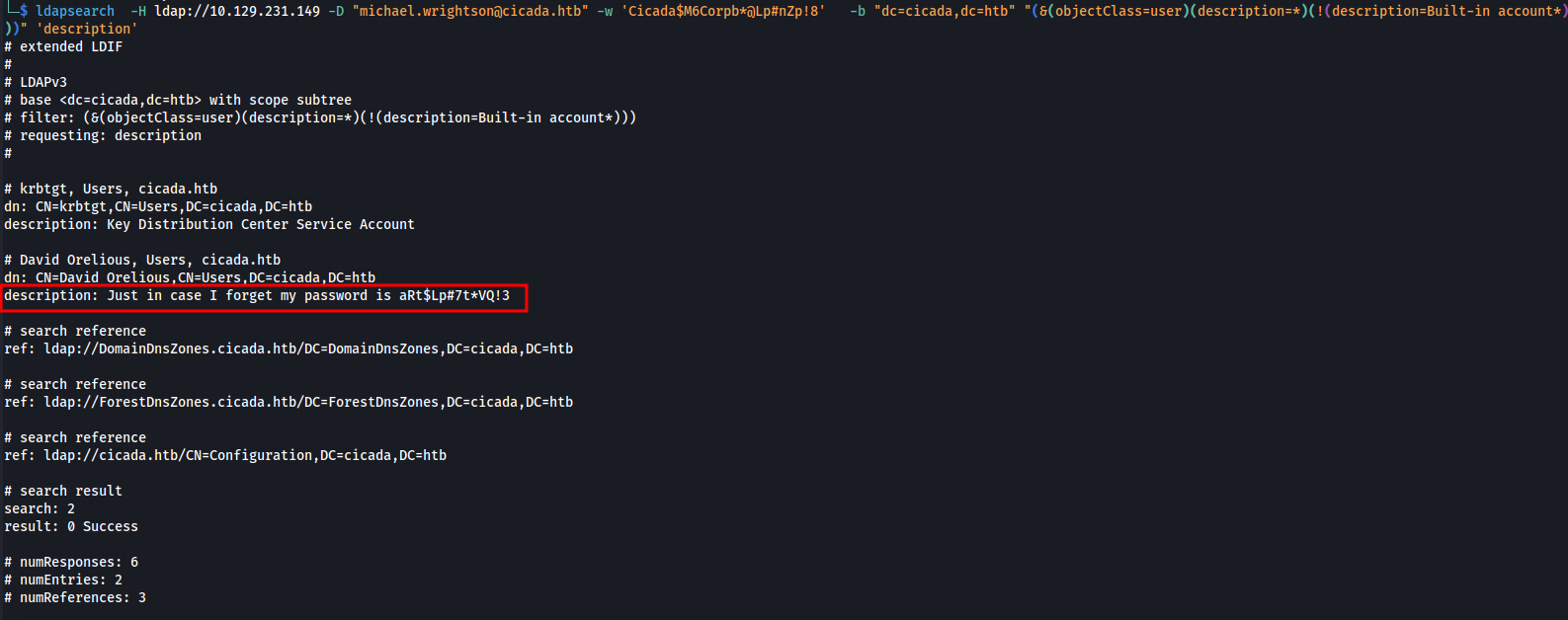
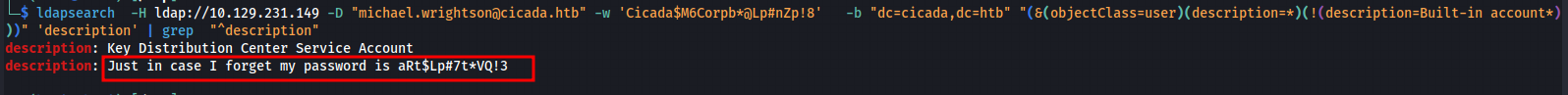
The final command was
ldapsearch -H ldap://10.129.231.149 -D “michael.wrightson@cicada.htb” -w ‘Cicada$M6Corpb*@Lp#nZp!8’ -b “dc=cicada,dc=htb” “(&(objectClass=user)(description=*)(!(description=Built-in account*)))” ‘description’ | grep “^description”
3. Other use cases
While exploring additional use cases, I thought about extracting LAPS passwords from computers (if you have the necessary privileges) or enumerating users with SPN (Service Principal Name) attributes set. Here are the commands:
- Extracting LAPS passwords:
ldapsearch -H ldap://10.129.231.149 -D “michael.wrightson@cicada.htb” -w ‘Cicada$M6Corpb*@Lp#nZp!8’ -b “dc=cicada,dc=htb” ms-mcs-admpwd=*” ms-mcs-admpwd
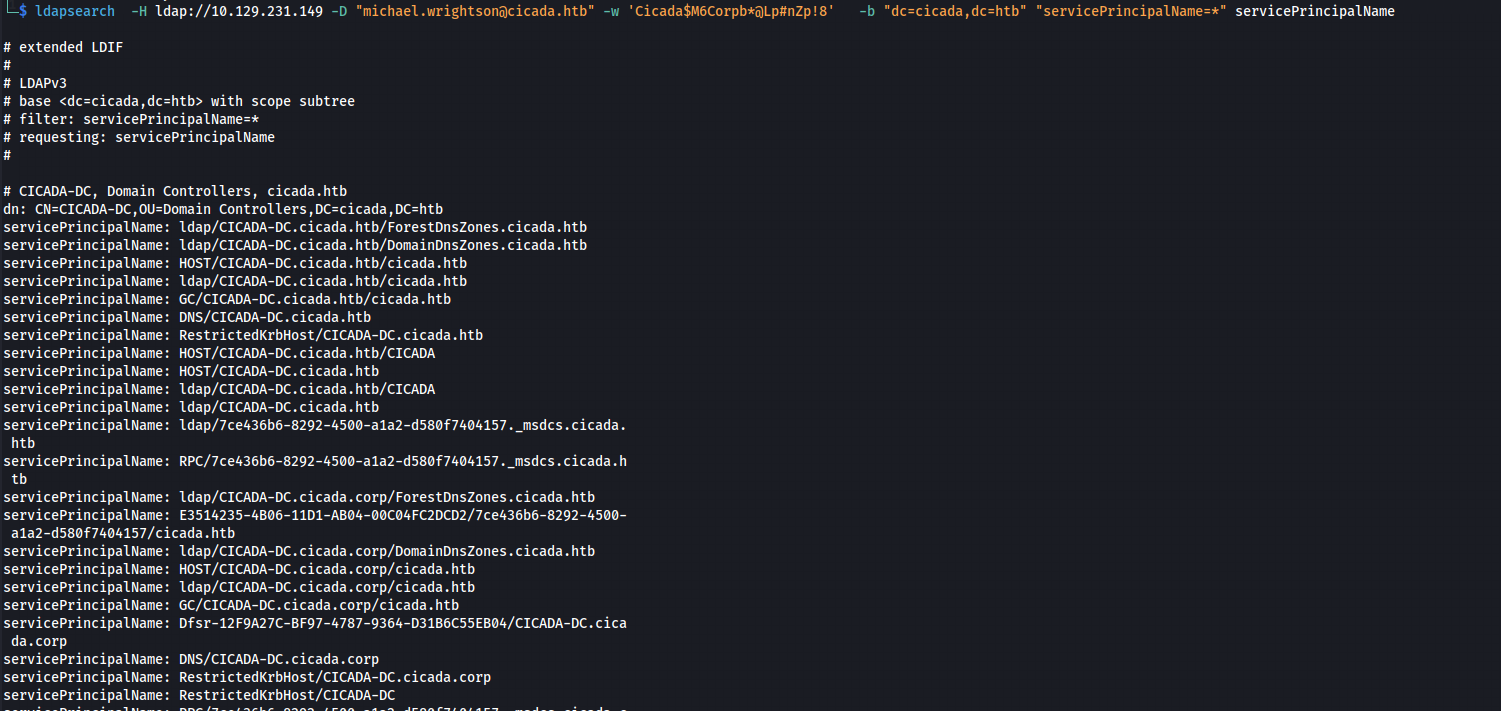
- Enumerating users with SPN attributes:
ldapsearch -H ldap://10.129.231.149 -D “michael.wrightson@cicada.htb” -w ‘Cicada$M6Corpb*@Lp#nZp!8’ -b “dc=cicada,dc=htb” “servicePrincipalName=*” servicePrincipalName
4. Benefits of using ldapsearch
Although some may find LDAP querying complex, it can be extremely useful for advanced searching tasks. In this article, I’ve shared some basic use cases, but ldapsearch can be used for more advanced queries, such as searching for users with password never expires enabled, searching for users in a specific department, searching for disabled users and much more.
In my view, the main benefit of using ldapsearch is its flexibility, as it allows you to customize requests exactly as needed.
I hope you find this tool useful in your assessments.
References :
- https://gist.github.com/jonlabelle/0f8ec20c2474084325a89bc5362008a7
- https://github.com/byt3bl33d3r/CrackMapExec
- https://github.com/PowerShellMafia/PowerSploit/blob/master/Recon/PowerView.ps1
- https://github.com/fortra/impacket/blob/master/examples/GetADUsers.py
- https://github.com/ropnop/windapsearch