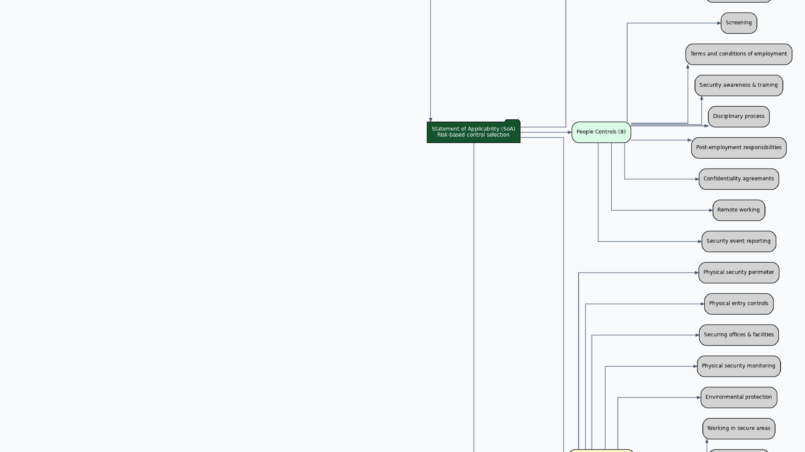
This mindmap presents a structured overview of the implementation of an Information Security Management System (ISMS / SMSI) in accordance with ISO/IEC 27001, following a Lead Implementer (LI) perspective. It illustrates the...
Archive - December 2025
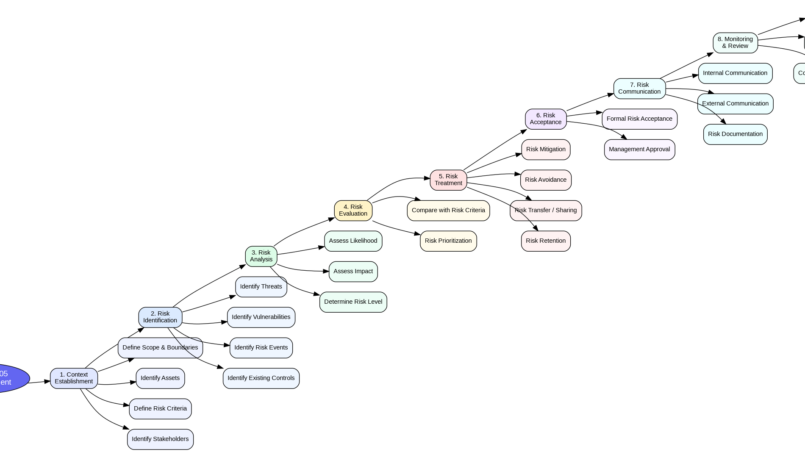
This mindmap summarizes the ISO/IEC 27005 risk assessment process by presenting its main steps and how they are logically connected. It starts with context establishment, where the scope, assets, stakeholders, and risk criteria...
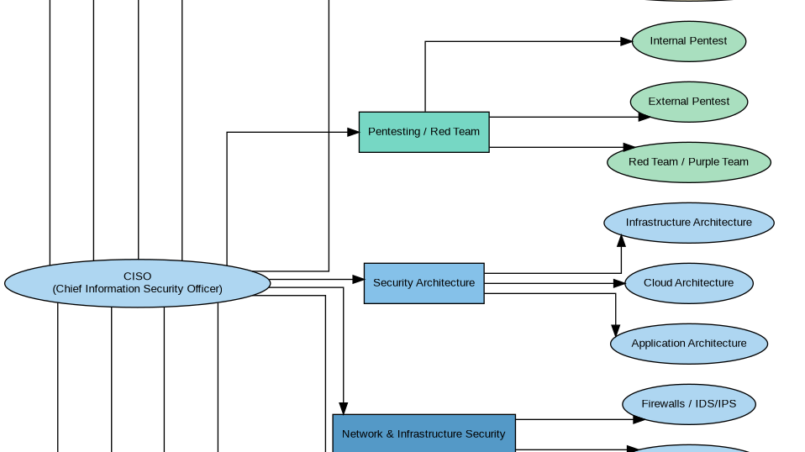
This mindmap provides a high-level overview of the main security domains a Chief Information Security Officer (CISO) typically reviews within a company.It illustrates how cybersecurity is not limited to technical controls, but...
Active Directory (AD) remains one of the most targeted components of corporate infrastructures. Due to its central role in authentication, authorization, and trust management, a single weakness in AD can quickly lead to full...